Design research, strategy and development for Google sigstore, a globally adopted signing and verification standard, since named by the White House as a key global security infrastructure.
“Working with IF is a pleasure. Their high quality of work, unique methodologies and ways of working meant we could accelerate our products in a way that I’ve not seen with other teams.”
[.quote-author]Product Manager, Google Open Source Security[.quote-author]
Problem
Today, software is mostly insecure. From a business perspective, insecure software is more expensive to maintain and consume - for everyone. Making software safer requires trust and adoption from developers globally. But trust is hard to earn.
Google, along with collaborators across the Open Source Software security community, have been developing tools to improve software security and therefore reduce costs, including for themselves. But to make these tools really successful, Google needed to make them understandable, usable and useful for more organisations.
We began working with the sigstore team. They had code, a basic website and a big ambition. Sigstore offers a responsible technology that has the potential to radically improve supply chain security. Although it was in early-stage development, we thought it could become infrastructure for the internet if widely adopted.
Our job was to understand why technical teams would use sigstore, what was stopping them from doing so, and how to translate the existing plans into something more user centred and accessible. Ultimately we wanted sigstore to be a trusted standard for signing and verifying software.

Our approach
Design research
We wanted to understand the open source developer community and their needs for software signing. We made prompts and took them into exploratory research sessions to test ideas and uncover insights. We emphasised speaking to historically under-represented developers upfront in our research to ensure that what we design supported their needs, to scale the ambition of the different products and services. This work expanded the sigstore’s team awareness and knowledge of their ecosystem of users, and what they needed. We gathered insights that drove the wider strategy, which established sigstore at the leading edge.
Alongside this research we expanded our field of view to include the wider ecosystem of Sigstore users and stakeholders. Working closely with the Sigstore team, we set up a participatory and open approach to the project to build credibility and alleviate any concerns about how an open source project was sponsored by a private business.

Hype free digital strategy
Over the course of a discovery and following beta we developed a digital strategy for sigstore that focussed on:
- helping users understand the benefits and uses of sigstore
- how it could be made most accessible
- what it meant to set the open source project up for success, in the long term.
This strategy was also made available to the open source community, and helped create and maintain alignment.

Full stack design and development
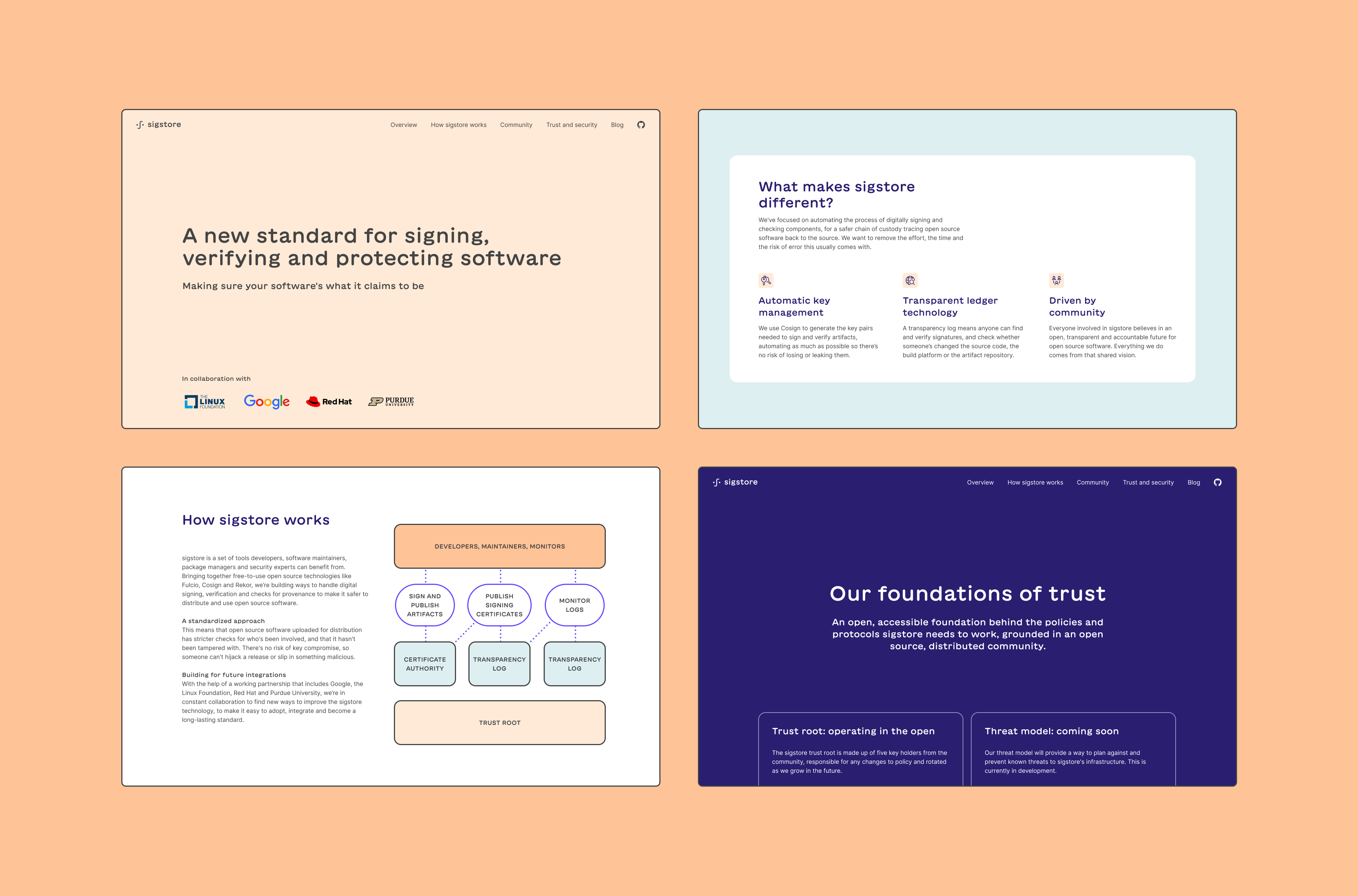
Over the course of several projects we designed, wrote content and built sigstore.dev. This increased credibility, trustworthiness, and clarity of purpose around sigstore while providing opportunity for continued improvement.
We also made docs.sigstore.dev and a process for contribution. For the first time the Sigstore community had an easy way to engage and contribute. Adoption took off. The work continued as we also helped the Sigstore team with similar work on slsa.dev and security scorecards.

Outcomes
The sigstore team made a global impact. With their revised proposition, website and tooling companies like Github and Kubernetes adopted sigstore and the project saw >100% growth in active contributors. The open source community grew to over 70 orgs and 500+ individuals contributing to +10M log entries. Adoption continues to grow.
Sigstore continues to be incorporated into a range of programming languages and developer ecosystems, and it was quoted by the White House presidential order as a key infrastructure project for global security. It now secures a software marketplace valued at $2B+.
"Sigstore has rapidly become the standard for signing, verifying, and protecting software"
[.quote-author]TechCrunch[.quote-author]
While this work is delivered in the form of products and services, the issues they touch on represent deep, philosophical change at a systems level. They influence and inform bigger policy decisions that sit across company and state boundaries.
Heading 1
Heading 2
Heading 3
Heading 4
Heading 5
Heading 6
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
- Item 1
- Item 2
- Item 3
Unordered list
- Item A
- Item B
- Item C
Bold text
Emphasis
Superscript
Subscript

